0ctf_2017_EasiestPrintf
0x01 分析
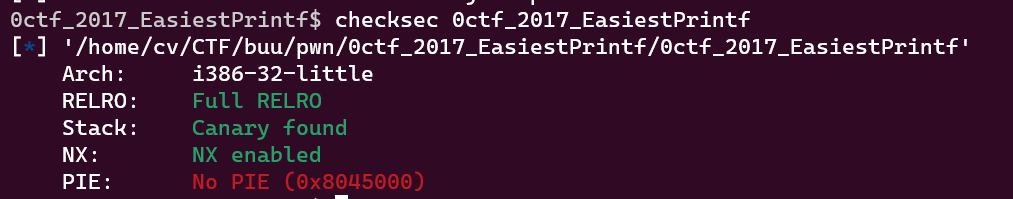
- 没开PIE
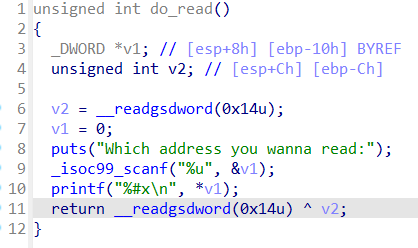
- 可以leak任意地址指向的数据
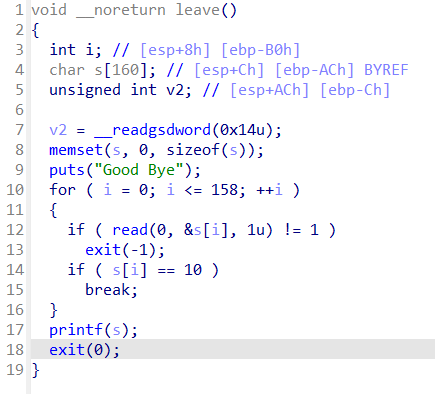
- 存在格式化字符串漏洞
0x02 利用
- 首先leak got表指向的libc函数地址
- 利用格式字符串漏洞修改__malloc_hook位one_gadget
- 通过printf打印超过65536个字符来调用malloc
0x03 Exp
1 | |
0x04 总结
- printf打印超过65536个字符时,内部会调用malloc
0ctf_2017_EasiestPrintf
https://www.w4y2sh3ll.top/2022/12/07/buuCTF-pwn-0ctf-2017-EasiestPrintf/